Scenario
You are acting in the role of Network Security Consultant, and you have been approached by the manager of the Company Smart Living spaces to look at the security of their products. Smart Living spaces is a company designing and building smart homes. According to the Oxford Dictionary, a smart home is a “home equipped with lighting, heating, and electronic devices that can be controlled remotely by a smartphone or computer”.
The smart home is a combination of devices that communicate with each other over a wired or wireless connection. The idea of a smart home (called as well Home Area Networks) is the ability for the owner of the home to be able to communicate with his appliances remotely, where the devices provide updates of current situations within the home, instances where the Laundry is ready, there is not enough milk in the refrigerator or the current temperature of in and outside the house, also how much energy has been used within the home.

Figure 1 General architecture of Home Area Networks
The company Smart Living spaces are located in Derby and receives a good range of customers, even businesses that decide to create a smart office environment.
The company offers a different kind of solutions in helping people to control their homes, allowing them and their homes to be smarter and better connected:
- Control TVs from their phones or tablets,
- View energy usage through smart thermostats,
- Control lights,
- View security cameras from their phones
- And even unlock the doors with their NFC and Bluetooth enabled phones.
Smart homes have the potential to improve the accessibility of technology, allowing users to control aspects of a room through their devices, this can provide help for both individual users and organisations. Moreover, smart home technology could be especially useful for people with disabilities, allowing them to control their homes from a single device. Smartphones are now both a remote control for the world around us and a dashboard providing us with a view of different services and notifications.
Note that most of the technology within the smart home has come out of the enterprise market and large office spaces where the management of lighting, heating, and access is key. In smart offices, an entire building can be monitored from a tablet, for example by offering to view the status of what lights are on, what doors and windows are open, and the state of security systems.
Although smart connected technologies have the potential to ensure home security, it has created new security challenges and issues. Both service providers and customers have different security needs. The service provider wants to be sure that the end customer cannot inappropriately manipulate a controller or attack a service portal. On the other hand, customers want to be sure that the service provider does not compromise their privacy.
Network Security Design
You need to access the risks of the network and proposed possible improvements that could be implemented on the network to defeat or minimise the current known threats. You need to produce a report about this for the managing director.
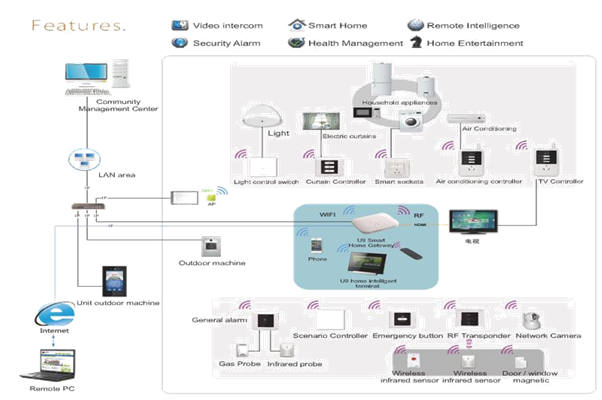
Figure 3 The layout of smart home network II
Requirements:
Your report document must include the following sections:
- An introduction that lays out what is the objective of the report (Note: the scenario should not be copied into the report).
- The body of the report should have the following content structured in an appropriate way:
- Identify the risks and vulnerabilities of one of the existing smart networks.
- A critical evaluation of the various solutions that can be used to try to remove the identified risks and vulnerabilities.
- When there is more than one solution to a given weakness, you need to discuss the strengths and weaknesses of each of the different approaches. A final recommendation should be clearly identified.
- You need to come out with a design of the newly secured network. An improved diagram of the newly proposed secured network needs to be included in the report.
- A conclusion to summarise your findings and to propose recommendations for future improvement.
- Support your arguments within the report with at least 8 good academic references.